Cyber threats are evolving, making Online Assignment Writing Services in the UK a reliable resource for students tackling cybersecurity topics. From NIST frameworks to Wireshark packet analysis and ransomware mitigation, understanding these concepts is crucial. Rapid Assignment Help provides expert guidance to ensure well-researched, high-quality assignments in this complex field.
The NIST Cybersecurity Framework performs a essential position in defensive virtual assets and personal statistics in state-of-the-art related society by using presenting corporations with a hazard-based totally method to coping with cybersecurity. As it defined in the creation, cybercriminals follow a careful plan and undergo numerous degrees referred to as the kill chain & quot ; before launching an assault. The NIST framework acknowledges this evolving chance panorama and offers companies with steering on threat assessment, asset safety, malicious hobby detection, incident reaction, and attack recuperation. The NIST Cybersecurity Framework describes a bendy, chance-based technique that permits agencies to personalize their cybersecurity packages primarily based on their individual danger profiles and tolerances. This is vital due to the fact it recognize that every company's information structures, vulnerabilities, and danger appetite can vary substantially. A blanket mandate or recipe is neither realistic nor powerful. More specially, this framework allows companies systematically examine cyber risks in their structures, belongings, facts, and skills. This consists of identifying threats, reading vulnerabilities, determining capability effect and possibility, and using this analysis to prioritize moves. Organizations can adapt by way of categorizing their systems and records, choosing core security controls, and determining responses to mitigate high-precedence dangers. For example, corporations with massive amounts of sensitive consumer records may also prioritize more potent get right of entry to controls, encryption, and pastime tracking. On the alternative hand, people with older legacy structures may attention on system enhancements and backups. Essentially, a risk-based totally technique presents context-primarily based autonomy while providing quality exercise requirements to manual improvements. This permits clever agencies to get the maximum value from their cybersecurity investments in step with their own tolerances, constraints, and goals. Specifically, this framework consists of 5 concurrent features: identify, guard, come across, reply, and recover. The Identification feature is centered on increasing an enterprise's understanding of a way to manipulate cybersecurity dangers. This includes asset control, chance assessment, and impact evaluation. Protection describes safety features that help ensure the provision of critical offerings which Identity and Access Management, Data Security, Protection Technologies and Policies. Detection capabilities provide a way to discover cybersecurity events in a well timed way through a continuous tracking and detection system. Response abilities include appropriate activities to take action on detected cybersecurity incidents. Finally, recovery competencies identify the suitable sports had to hold resilience and restore functionality suffering from the incident. The NIST framework's five concurrent talents provide a high-level strategic view of coping with cybersecurity risks to an organization's human beings, processes, and generation. These functions recognize that mere precautions are not enough. Organizations also need danger focus, non-stop monitoring, mitigation plans, and the capability to renew operations. The framework facilitates a proactive in preference to reactive approach by means of enabling businesses to view all 5 domain names collectively in preference to in silos, and powerful cyber threat management requires emphasizes the need for continuous and simultaneous adjustment of the features of the Introducing controls in simplest one or areas creates incomplete protection and exposes gaps. In summary, the NIST framework recognizes that no employer can prevent all assaults. However, through offering a flexible threat-based approach that may be tailor-made to an enterprise's wishes, organizations can determine their chance tolerance, enforce suitable security measures to guard essential property, and protect in opposition to malicious attacks. Detect interest, reply to incidents, and get over assaults. Therefore, it performs an vital function in protective touchy information and retaining privacy in state-of-the-art virtual age.
Get assistance from our PROFESSIONAL ASSIGNMENT WRITERS to receive 100% assured AI-free and high-quality documents on time, ensuring an A+ grade in all subjects.
Wireshark is an open-supply community protocol analyzer that cybercriminals can use to acquire touchy data approximately a target's community for the duration of the reconnaissance section of an assault. Specifically, Wireshark allows an attacker to capture and investigate all traffic passing thru a network phase. By putting the network interface of a tool walking Wireshark into promiscuous mode, the tool can covertly intercept and record all community packets, even those not intended for that tool. Wireshark allows comprehensive network reconnaissance through an attacker in 4 important methods: First, Wireshark allows mapping of the goal's network topology with the aid of intercepting site visitors among gadgets and revealing her IPs, hostnames, domain names, subnets, routers, and related systems. This absolutely exposes the format of your infrastructure.
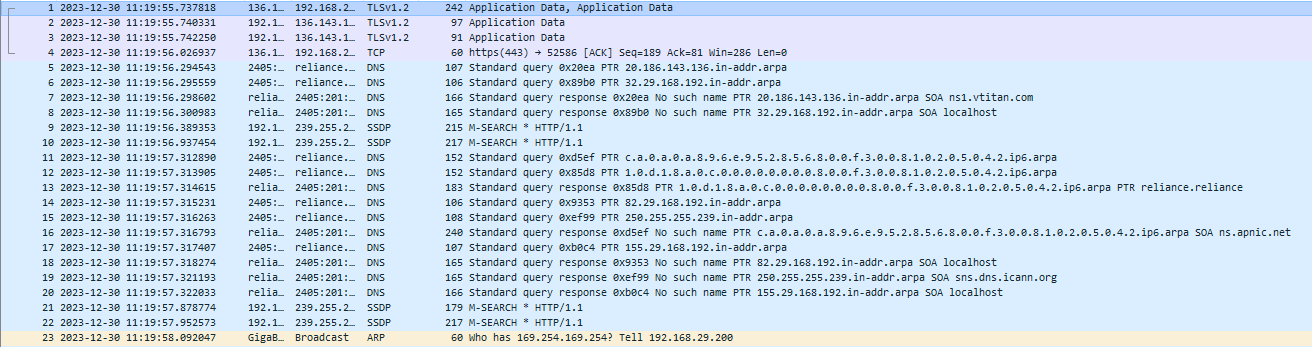
Figure 1: Data table of the various protocol
(Source: Self-created in Wireshark)
Then, by way of searching at open ports and communication, Wireshark determines what working device, provider version, mail server, database, and so on. Attackers find goals to make the most. Third, unencrypted HTTP, FTP, Telnet, and other protocols can permit direct eavesdropping on usernames, passwords, files, and touchy periods. This permits brazenly transmitted information to be stolen. Finally, tracking common styles in the amount of visitors among network segments can tell attackers about such things as height utilization instances and big transfers. These planning insights support green assaults. In brief, Wireshark provides dangerous insights into your goal's humans, tactics, technology, their patterns, systems, and statistics flows. This makes it less difficult for attackers to perceive vulnerabilities. Although Wireshark has valid makes use of, it's far important to put in force strong encryption and pastime tracking to limit the interception of unauthorized traffic. Allowing such network mapping is an essential first step in addressing the risk of cyberattacks.
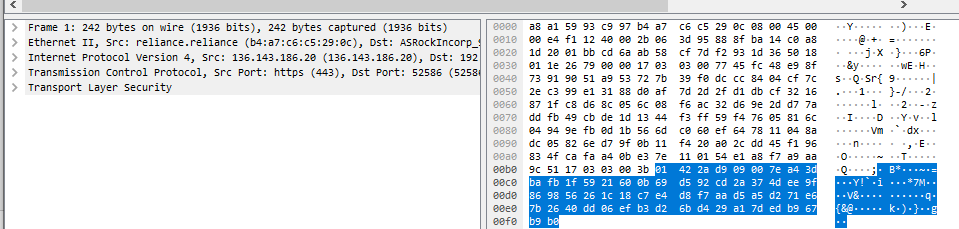
Figure 2: output
(Source: Self-created in Wireshark)
WannaCry ransomware makes use of an NSA-advanced take advantage of called EternalBlue to unfold to inclined Windows structures thru the SMB file sharing protocol. The virus propagates by scanning publicly reachable SMB ports throughout the network, sending maliciously crafted packets to make the most Windows vulnerabilities, and remotely executing code. . This self-propagation lets in it to quick infect whole network segments. Once set up on a machine, WannaCry encrypts masses of various file kinds, ranging from Microsoft Office files, databases, and emails to photographs, movies, source code, and more. It encrypts your documents using AES and RSA encryption and basically locks and hijacks your valuable data. The simplest manner to retrieve the facts is with a private key owned with the aid of the malware writer. Then they blackmail the sufferer and demand ransom payment in cryptocurrency Bitcoin to provide this decryption key. By compromising essential records and disrupting commercial enterprise operations, WannaCry makes use of strong encryption to pressure companies to pay large ransoms to regain access.
TeleRAT is a socially engineered faraway get entry to Trojan that tricks customers into downloading infected far flung computing device apps. When enabled, it contacts the command server for instructions even as the usage of custom protocols and random ports to avoid detection. TeleRAT gives cybercriminals complete surveillance and manipulate through features together with webcam and microphone viewing, keystroke logging, statistics distribution, and information destruction. To include TeleRAT, educate customers about malicious apps, limit the set up of unauthorised far flung gear, use modern-day antivirus gear to trap acknowledged Trojans, and become aware of suspicious Trojans that indicate a records breach. You want to screen your structures for interest and analyse community connections to come across and apprehend anomalous outbound communications. TeleRAT spreads via social engineering, tricking customers into downloading a malware-inflamed remote get admission to app. Once energetic, it connects to a command server for instructions and makes use of custom protocols and random ports to avoid detection. This permits for whole faraway tracking and manipulate, from webcam viewing to keylogging to records distribution and destruction. To stop TeleRAT, educate your users about malicious apps, restrict unauthorized far off apps, use an updated antivirus software to capture known Trojans, and make sure there may be no suspicious excessive pastime. You want to reveal the gadget and analyse network site visitors to discover anomalous outgoing connections which are working underneath command and manage cues. Defenses extensive throughout people, procedures, and technology are critical to fighting superior persistent threats like TeleRAT, which integrate social, business, and assault technologies.
References
Journal
1.0 Introduction - How Effective Is Pulmonary Rehabilitation In Improving The Quality Of Life Among Copd Patients? Say goodbye...View and Download
Question. 1: Research paper analysis Rapid Assignment Help delivers excellence in education with tailored Assignment Help,...View and Download
Part 1: Understanding NIST, Wireshark, and Ransomware Threats Cyber threats are evolving, making Online Assignment Writing...View and Download
Question 1: Regulatory framework and financial reporting standards Make your assignments stand out with our...View and Download
QUESTIONS Enhance your knowledge and skills with Affordable Online Assignment Help Experts, ensuring high-quality academic...View and Download
QUESTION 1 Enhance your academic performance with Professional Assignment Help for All Subjects. Get expert guidance,...View and Download
Copyright 2025 @ Rapid Assignment Help Services
offer valid for limited time only*

