Join thousands of satisfied students who trust Rapid Assignment Help for their academic needs through top-notch Assignment Help.
Regarding the impact of the control variables on a country's financial and economic criminal behavior index, researchers find convincing evidence of the contributions of economic development, governance quality, tax load, unemployment, quality of audits, press freedom, religion, and country of origin (Achim, Borlea & V?idean, 2021). Financial crime and illegal behavior adapt to developments in the sectors that they prey upon. Due to the rising automation and technological sophistication of financial organizations, these crimes have become more impersonal. One series of crimes that precisely exemplifies the cyber characteristics associated with the majority of contemporary laundering of money and forgery began in 2013 and is known as the "Carbanak assaults." According to Hasham, Joshi, and Mikkelsen (2019), malware was used to steal nearly $1 trillion from banks. To get access to the systems, the attackers utilized phishing. They then moved artificially inflated funds to their own accounts and either programmed ATMs to dispense cash to waiting allies.
Get assistance from our PROFESSIONAL ASSIGNMENT WRITERS to receive 100% assured AI-free and high-quality documents on time, ensuring an A+ grade in all subjects.
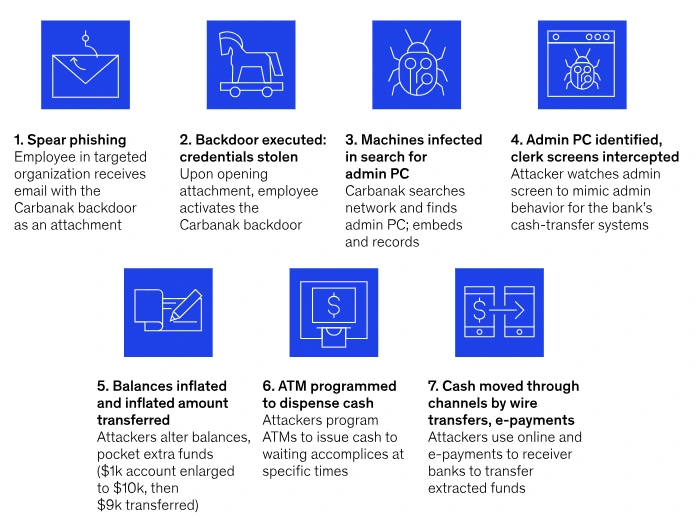
Figure 1: Cyber fraud profile illustration through the Carbanak attack
Notable is the fact that this crime consisted of a lone, well-thought-out assault on multiple banks. The attackers showed a great awareness of the online environment, and it is likely that they were aware of banking practices, security precautions, and even the dangers associated with siloed organizational and governance structures. They also employed a range of techniques, including ATMs, debit or credit cards, wire transfers, and other tools.
New technologies are altering the fight against illicit financial transactions, assisting reputable sector players in eradicating corruption while also opening up new chances for criminals to profit from. As per the research by Bodescu, Achim & Rus (2022), the rise in digital technology reduces the likelihood of monetary laundering.
According to Technology-Enabled Crime Theory, understanding and managing relatively complicated criminality might be challenging at first, and there is ongoing struggle between law enforcement and the criminal element for technological superiority (Akdemir & Lawless, 2020).
AI and ML are useful tools in the battle against financial crime because they may be used to spot patterns and discrepancies in financial transactions. Anomaly detection, for instance, can spot odd financial transaction patterns that might point to fraud. As found by Kute et al (2021), network analysis can reveal connections between parties involved in financial transactions, assisting investigators in identifying intricate financial crime schemes. Utilizing predictive modeling, historical data can be examined to spot possible financial crime threats and take preventative measures before they materialize. In an effort to better identify and stop financial crimes, HSBC Bank adopted an anti-money laundering system fueled by AI (Ray, 2021). Millions of transactions were examined by the system in real time, and trends of behavior that suggested possible money laundering activity were found. The algorithm was able to identify patterns of questionable activity that were previously unknown and flag them to require human inspection, significantly improving the bank's capacity to identify and stop financial crimes.
A distributed ledger made possible by blockchain technology enables for the safe, open, and impenetrable recording of transactions. It provides a decentralized system suitable for a range of uses, including financial transactions. Immutability, decentralization, and openness are a few characteristics of blockchain technology that make it effective in the fight against financial crime.
Decentralization makes it possible to do away with middlemen and lower the danger of fraud (Nabilou, 2019). Once a transaction is added to the blockchain, it cannot be changed or removed because of immutability. Every member of the network has access to the transaction history thanks to transparency, which makes it simpler to identify and look into any fraudulent behavior.
Together, the nodes in a blockchain system validate and verify transactions to make sure they are valid and follow the network's rules. It is challenging for an attacker to change the blockchain ledger without being noticed by the other nodes because every node has a copy of the whole ledger.
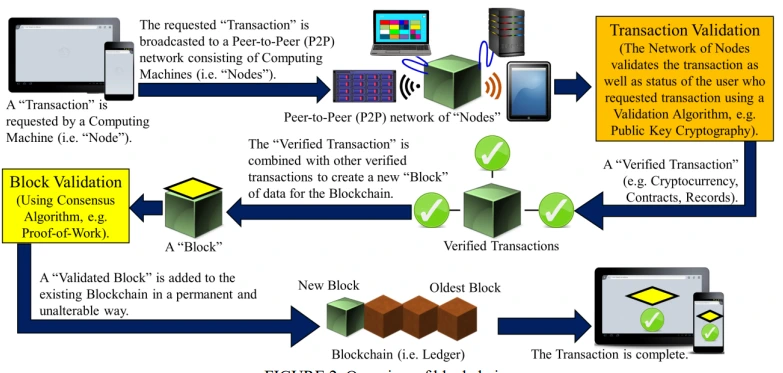
Figure 2: Transaction securely using blockchain nodes
Each transaction generates an output that can be redeemed by the intended recipient nodes indicated by the public key hash associated with the transaction. This public key hash protects users' privacy while authenticating users by uniquely identifying them within the network (Puthal et al, 2018).
"Know Your Customer" and "Anti-Money Laundering or AML" compliance are two of the most important ways that blockchain technology is being used to fight financial crimes (ACAMS TODAY, 2019). Financial institutions may safely and effectively verify customer identities by developing a blockchain-supported KYC platform. This will stop fraudsters from utilizing fictitious identities to engage in illicit activity.
Another crucial use of this technology in avoiding financial crime is smart contracts. The details of the contract between the buyer and seller are directly encoded into lines of code in these self-executing contracts. By automating and enforcing contractual commitments, smart contracts can lower the risk of potential fraud and guarantee that regulations are followed.
Blockchain technology can be extremely useful in the domain of "computerized identity verification", which helps to avoid financial crimes. Digital verification of identity systems built on the blockchain can safely and precisely confirm people's identities, lowering the risk of money laundering and fraudulent activities. In both the broader public and private industries, the financial services sector is leading the revolution in digital identity (ACAMS TODAY, 2019). Using the GOV.UK Verify platform as an example, deposit-taking institutions, or banks, are simultaneously participating as data suppliers in publicly managed digital identification networks.
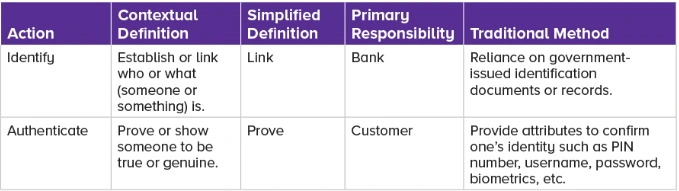
Figure 3: Key actions for identification and authentication
It is expensive and time-consuming to match attributes and trace identities. Traditional approaches to accomplishing such tasks demand a large investment in both human and technological resources. Additionally, this procedure is carried out internally, and its value comes almost exclusively from reducing the danger of financial crimes; as a result, there is little financial value created in carrying out this activity; rather, it is a preventative measure to guarantee regulatory compliance and financial stability (ACAMS TODAY, 2019). As network participants work together to cut expenses and also generate income for those institutions that still complete the identifying procedure, much of the friction experienced in the traditional scenario is eliminated when switching to a digital identity solution.
Whether you're studying microeconomics, macroeconomics, or econometrics, our economics assignment help covers everything, from fundamental theories to the latest economic models.
Financial institutions need to be especially concerned about cybersecurity because hackers are increasingly targeting them in an effort to take advantage of systemic weaknesses. Sensitive consumer information loss, financial asset loss, and reputational harm are all potential outcomes of these attacks. By using cutting-edge technologies, working together, and according to regulations, financial institutions can strengthen their protection against computer viruses and fraudulent operations (Shank, 2023).
In the age of digital finance, financial institutions still confront a number of dangers and difficulties despite the deployment of strong cybersecurity measures. As employees use systems from outside the office network, the prevalence of remote work has increased the risk of cyberattacks. The risk of a breach may also grow if third-party vendors and service providers are used.
With the existing technologies like AI, ML, NLP, and blockchain, the financial institutions will not only benefit but may also face challenges as criminals are also changing their attacking patterns by integrating smart techniques and technologies. As Bitcoin and digital technologies are increasingly incorporated into global financial institutions, there is an increase in the demand for digital forensics. A normal investigator can no longer see crimes because of the incorporation of blockchain technology.
Because of the processing capacity of computers and the speed of the internet, many crimes can now be performed in a matter of minutes rather than requiring months of careful planning and deception. According to Redding (2021), digital forensics has advanced to keep up with the complexity of crimes like embezzlement, money laundering, and insider trading to make the jobs of investigators easier. In light of how society has evolved and expanded cloud internet and technology services over recent years, the use of digital analytics in financial crime has increased dramatically. For instance, billions of business emails are sent every day all around the world. It would take years to get through all of these emails by simply clicking and scrolling. However, by keeping to the proper audit trail and applying digital forensic processing techniques, one can exclude material that is not pertinent to the case and advance the inquiry more quickly. As a result, analysts and investigators would be able to effectively and thoroughly investigate a limited amount of pieces of evidence to begin determining where or how the sum of cash that was taken was hidden, as well as who committed the crime based on artifacts and digital records found by the forensic tools. Finding recurring information sets that could be important clues in a case is another way that forensic computers can help.
Companies may easily develop tailored search profiles and uncover the evidence more rapidly during an inquiry by using digital forensics technologies. The investigators are also given the evidence in a concise report that details the data sources, typical evidence-laundering techniques, and an order of importance for the evidence. Akinbowale, Klingelhöfer, and Zerihun (2020) assert that financial crimes have become more sophisticated and difficult to detect.
The automation of repetitive procedures has been one of technology's most significant effects on accounting methods. Automation has made it possible to automate previously labor-intensive operations like entry of data, bookkeeping, and reconciliation, giving accountants more time to work on more involved projects like financial evaluation and strategic thinking (Lasnick, 2022). With the use of cloud-based software, businesses may access their financial data from any location with a web connection, doing away with the need for internal servers and cutting down on IT expenses. Accounting procedures have been significantly impacted by analytics and big data as well. Accountants may make accurate forecasts and wiser decisions by analyzing enormous volumes of financial data to find trends and patterns.
In major literature works it has been found that the use of technology in the battle against financial crimes has become indispensable. In order to stay one step ahead of financial criminals, financial institutions must keep up with the latest emerging technologies in the continuously changing field of financial crime and its identification and avoidance. There is a lot of potential to investigate and analyze how to improve efforts to prevent financial crime through the integration of machine learning, blockchain technology, and strong cybersecurity measures.
Financial institutions must put cybersecurity first if they want to safeguard both themselves and their clients from possible harm from online criminal activity. They may reduce risks and keep one step ahead of attackers by putting strong cybersecurity measures in place, such as authentication with multiple factors, data encryption, and penetration testing.
To protect their financial information and assets, financial institutions should adopt these advances in technology and implement them efficiently. It is critical to have efficient and effective approaches for detecting and preventing financial crimes given that the number and difficulty of these crimes are only going up.
References
Introduction Get free samples written by our Top-Notch subject experts for taking the Assignment Helper from Rapid...View and Download
Introduction Get free samples written by our Top-Notch subject experts for taking online Assignment...View and Download
Introduction Get free samples written by our Top-Notch subject experts for taking online Assignment...View and Download
Introduction - Cross-Cultural Management and Leadership Challenges Get free samples written by our Top-Notch subject experts for...View and Download
Introduction Get free samples written by our Top-Notch subject experts for taking online Assignment...View and Download
Introduction Get Free Online Assignment Samples from UK's Best Assignment Helper Experts to boost your academic...View and Download
Copyright 2025 @ Rapid Assignment Help Services
offer valid for limited time only*

